Enterprises will increasingly build operational command centers because they provide something dashboards cannot: continuous governance and coordinated enterprise response.
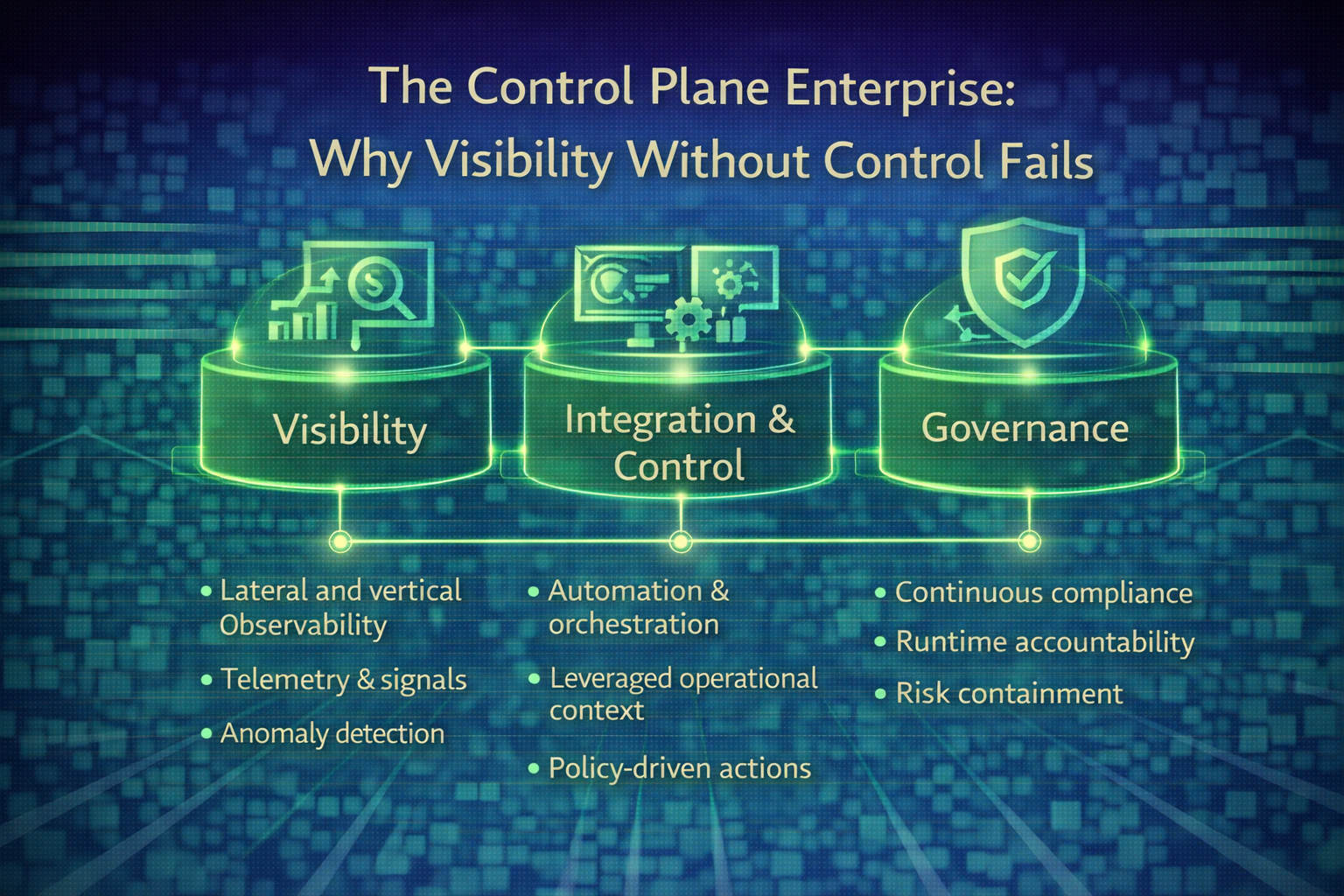
Read MoreEnterprises need an operating layer that converts signals into decisions and decisions into governed action. That is the enterprise control plane. Engineering Intelligence is the foundation that makes it possible.
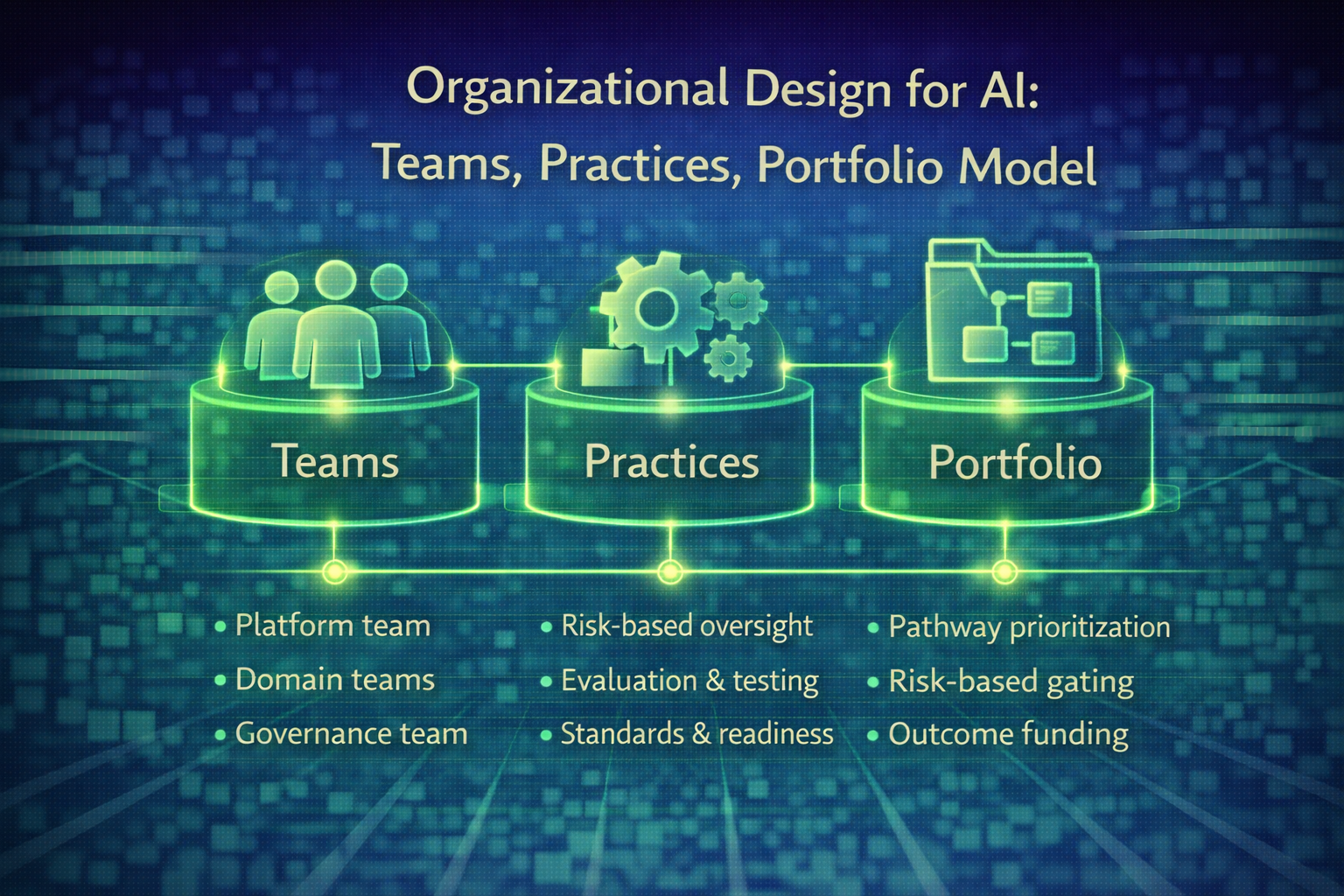
Read MoreWhy enterprises scale AI through operating model clarity, not through tools.
Read MoreWhy enterprise AI must be measured as a capability, not as a collection of pilots.
Read MoreTwo concepts have surfaced in quick succession that deserve attention from anyone making decisions about how their engineering organization relates to AI. Both are attempts to name something already happening and give teams a vocabulary for reasoning about it.
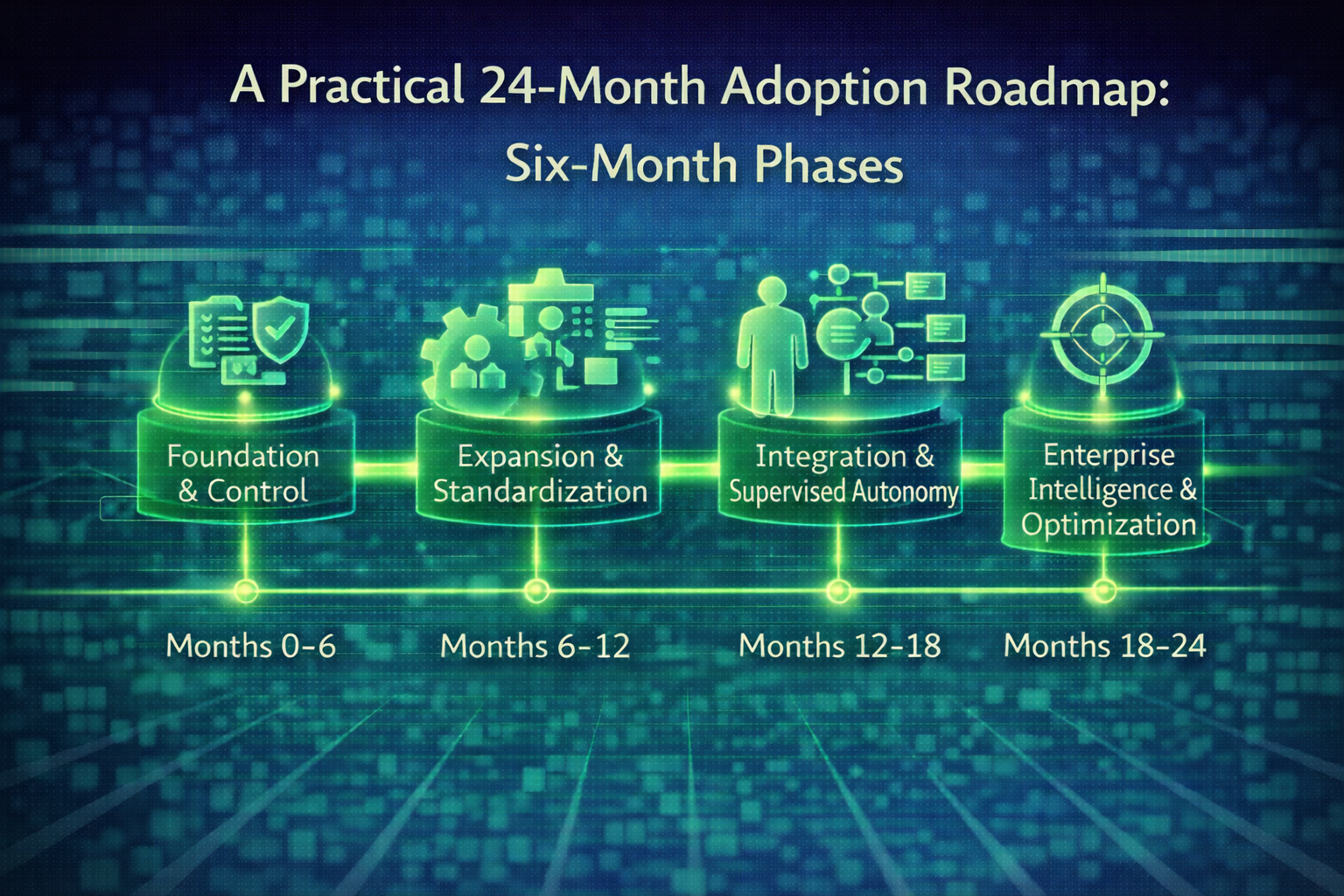
Read MoreWhy enterprise AI success depends on sequencing, operating discipline, and measurable trust.
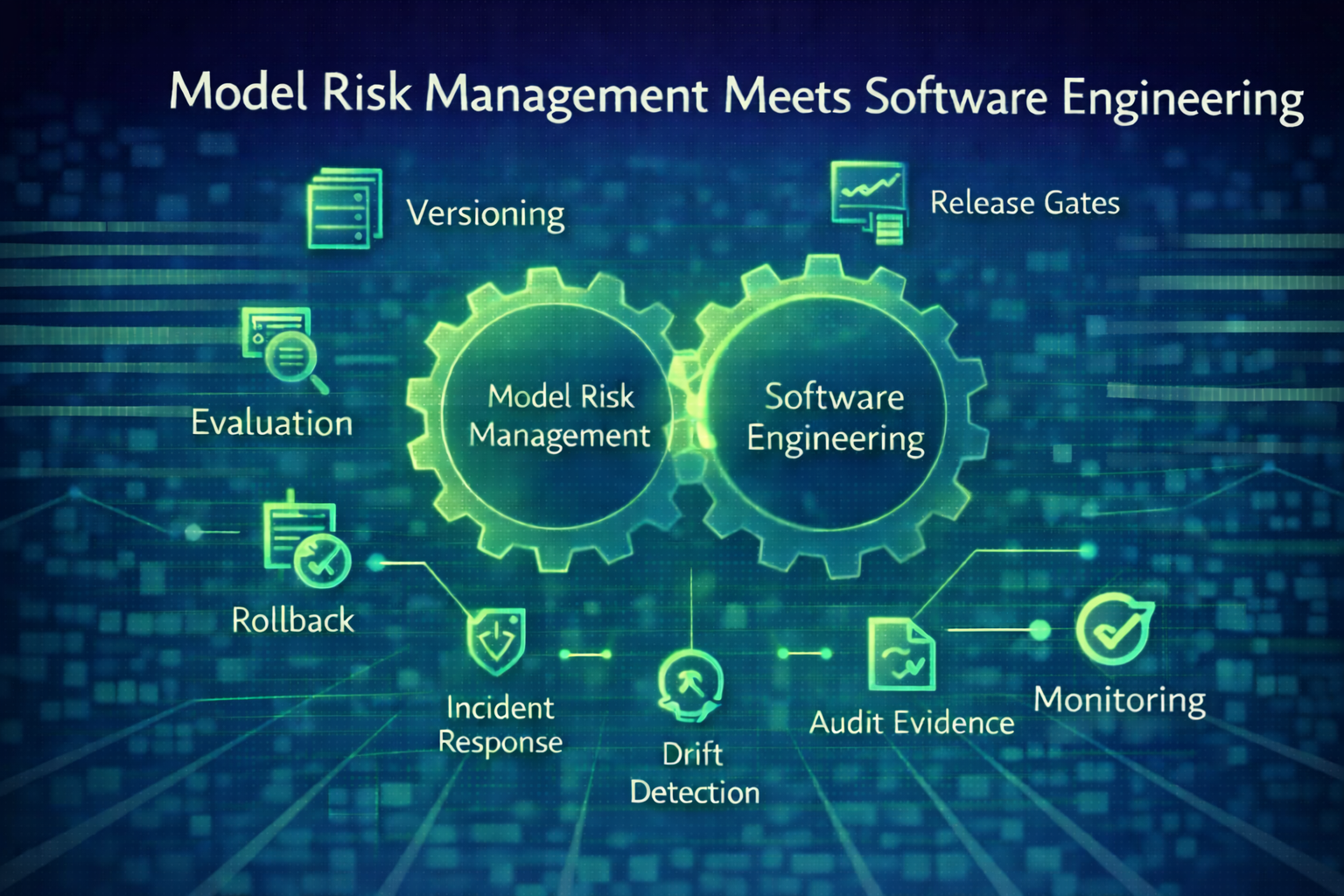
Read MoreWhy scalable AI requires the discipline of production software, not the looseness of experimentation.
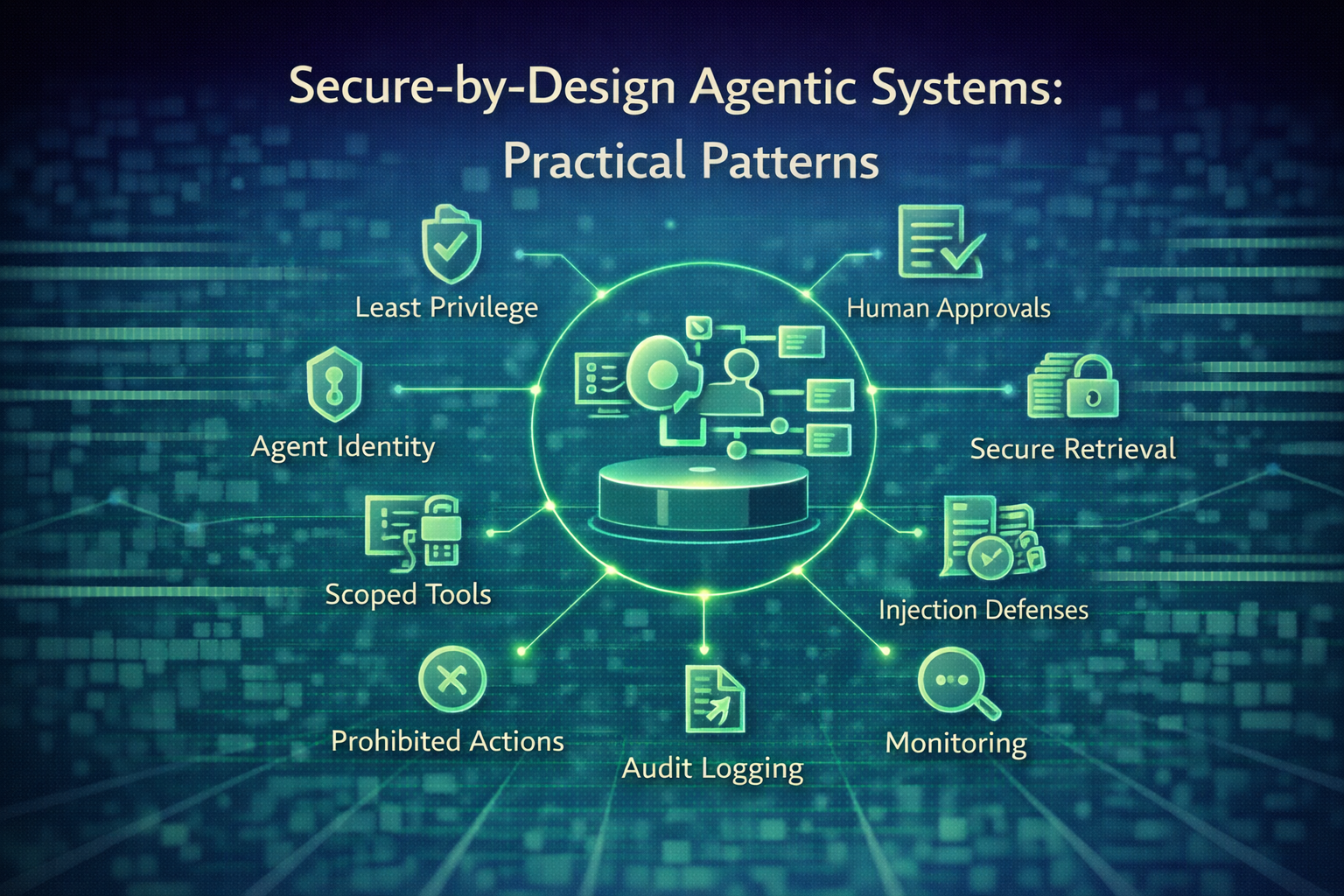
Read MoreWhy agentic AI must be treated as privileged infrastructure, not a productivity feature.
Read MoreWhy supervised autonomy is the operating model that makes enterprise AI scalable.
Read MoreAI at scale requires continuous control, not periodic oversight.
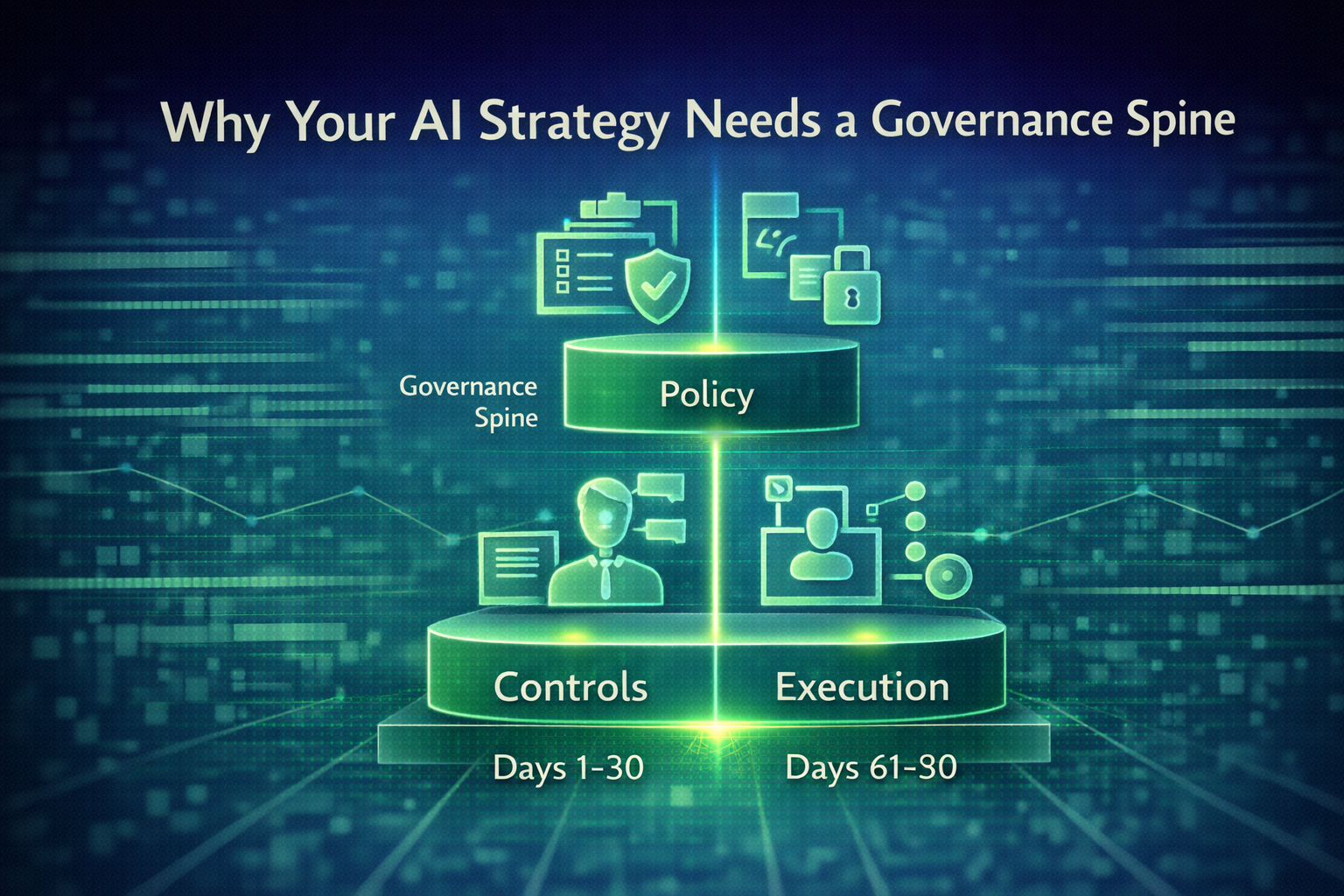
Read MoreWhy early discipline determines whether agentic AI scales into advantage or stalls into risk.
Read MoreThe enterprise workforce is changing. Not gradually, but structurally.
Read More